As a quick fix to protect your Windows server machines from the latest SSLv3 POODLE bug, please follow below steps on your Windows Server machine – these steps essentially disable the vulnerable SSLv3 protocol:
1) Open registry editor and navigate to
HKey_Local_Machine\System\CurrentControlSet\Control\SecurityProviders\ SCHANNEL\Protocols
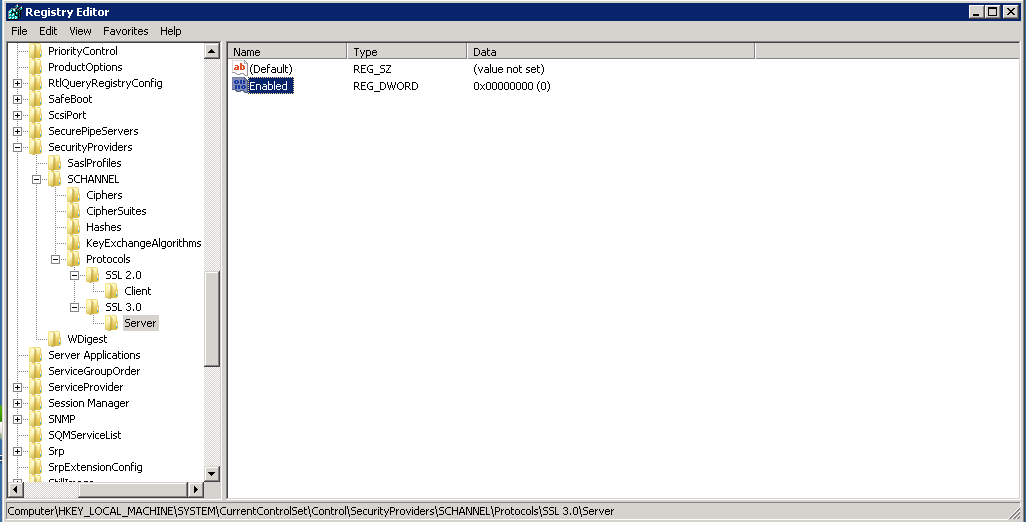
2) You will likely see an entry with SSL 2.0 key already created. You will need to create another key named SSL 3.0 alongside it. Thereafter create a sub-key named Server inside SSL 3.0 and inside it create a DWORD named Enabled and set its value to 0.
Your screen should look like below:
3) Create similar entry (Server -> Enabled -> 0) for SSL 2.0 as well.
Below are quick commands to perform above steps:
rem -- SSLv2 reg add "HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server" /v Enabled /t REG_DWORD /d 0x00000000
rem -- SSLv3 reg add "HKLM\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server" /v Enabled /t REG_DWORD /d 0x00000000
4) Reboot the server to apply new settings.